Every day we plug in, charge up, and connect — often without a second thought. But in today’s world, the smallest connection can expose the largest vulnerability. A simple USB port in a hotel room, airport lounge, or vehicle dashboard can silently transfer data, install malware, or compromise an entire device.
In New Zealand, cybersecurity experts have begun warning that this threat – once considered fringe – is now mainstream. In 2023, Radio NZ reported that many New Zealanders remain “surprisingly unaware” of the risks posed by public USB charging ports. Around the same time, the National Cyber Security Centre (NCSC NZ) and CERT NZ both advised that public USB stations may be compromised by cybercriminals, recommending the use of USB data blockers or charging-only cables as a simple physical defence.
As the NCSC NZ guidance puts it:
“Public USB charging stations may be compromised by cybercriminals to install malware or steal data. We recommend charging from mains outlets or using a USB data blocker where needed.”
In a society where mobile devices carry not just personal photos but entire digital identities, that warning is hard to ignore.

What Exactly Is a Data Blocker?
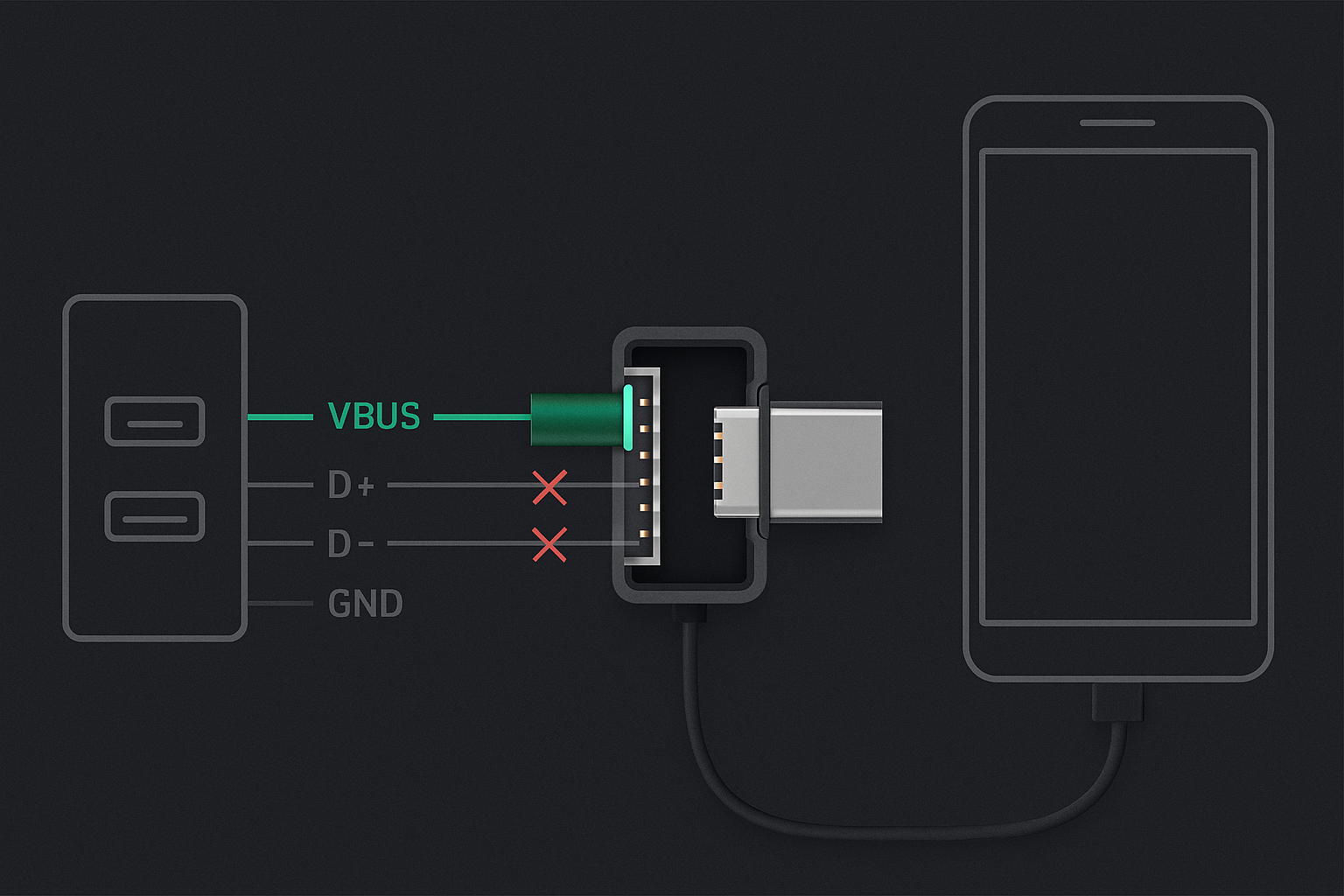
A data blocker is a small hardware adapter that connects between your device and a USB charging source. It allows electricity to pass through while physically disconnecting the data lines (the D+ and D– pins) that carry digital information.
Think of it as a one-way valve for power. Your phone or tablet charges normally, but no data handshake occurs – no device IDs, no file access, no hidden code injection.
High-quality data blockers, such as those designed by OffGrid, are tested to guarantee full data-line isolation and voltage stability across modern fast-charging standards. This matters: not all devices sold online are truly passive. Cheap imitations often include counterfeit chips or incomplete isolation, defeating their purpose and potentially introducing new vulnerabilities.
For law-enforcement and defence applications, OffGrid’s USA-made variants offer verified domestic manufacturing and anti-tamper assurance – critical where national security or evidence integrity are at stake.
The Expanding Attack Surface
As New Zealand becomes more connected, public USB charging points are appearing everywhere – airports, cafés, buses, rental cars, hotels. However, convenience brings risk…
Each port capable of delivering power is also capable of negotiating a “data handshake”. A compromised port or cable can exploit that brief moment of connection to install spyware or harvest data. The NZ Herald has reported multiple warnings about “phone-charging scams” at airports, where modified ports steal information the instant a device is plugged in.
The problem isn’t hypothetical. In 2023, CERT NZ echoed international alerts, advising travelers to avoid public USB stations and use their own chargers or data blockers instead. When both New Zealand’s national cyber agencies and its mainstream media start highlighting the same issue, it’s no longer niche – it’s a verified local risk.

Who Needs Data Blockers — and Why
Consumers – For everyday users, data blockers are a low-cost, highly effective layer of protection. Plug into an airport seat, café power strip, or hotel lamp – and your device remains safe from data theft.
In New Zealand, where mobile banking, two-factor authentication, and digital IDs are ubiquitous, a compromised smartphone can expose far more than personal photos. As RNZ noted, public awareness of this risk is still low, making education – and practical tools – essential.
For privacy-minded individuals already using Faraday sleeves or shielding pouches, a data blocker is the wired equivalent: physical privacy at the port level.
Corporate and Enterprise – Many New Zealand businesses operate globally. When staff travel and attend conferences, they will inevitably plug into whatever ports are available. For corporate IT managers charged with compliance under frameworks such as ISO/IEC 27001 or the NZ Protective Security Requirements (PSR), data blockers offer a tangible extension of digital policy – a hardware control that enforces the principle of Zero Trust.
Intellectual property, financial records, and client data are among a company’s most valuable assets. A single compromised connection can provide an attacker with a foothold inside a secure device. By issuing data blockers as part of employee travel kits, organisations demonstrate due diligence and strengthen both corporate security and employee confidence.
Government and Law Enforcement – Agencies across New Zealand rely on mobile and field-based devices for everything from evidence capture to communications. These devices often require charging on the move – in vehicles, temporary offices, or public buildings.
Without a data blocker, each of those connections becomes a potential ingress point. CERT NZ warns that malware can be delivered through modified USB hardware faster than endpoint protection can react. For investigators, that could mean contaminated evidence; for public servants, it could mean a breached device containing sensitive information.
By integrating data blockers alongside Faraday enclosures and shielded transport cases (like those from OffGrid), agencies can maintain both operational readiness and evidential integrity – ensuring the digital chain-of-custody remains unbroken.
Defence and Security – Operational security (OPSEC) in defence environments depends on absolute control of interfaces. Any external connection – wired or wireless – must be verified.
The Defence Force and its partners operate under stringent supply-chain integrity standards. Here, provenance matters as much as performance. OffGrid’s USA-made data blockers, provide precisely that: verified, tamper-evident construction suitable for mission-critical use.
When combined with shielded cables and Faraday enclosures, these blockers ensure that power delivery never becomes a pathway for data leakage – maintaining the integrity of communications and equipment in the field.
Digital Forensics and Cyber Professionals – For digital-forensics examiners, security auditors, and incident-response teams, data blockers are procedural tools, not accessories. During evidence processing or live triage, powering a suspect device always carries risk.
Using a verified data blocker ensures that power can be supplied without enabling any data communication, preserving both evidence and host system security. OffGrid products are already trusted by digital-forensics units within New Zealand’s law-enforcement community and by international partners, offering the same verified engineering standards across jurisdictions.

Why Quality Defines Trust
Security begins with assurance. Generic devices bought online may look identical, but inside they often contain cheap or incomplete circuitry – or even active chips that re-enable limited data functions.
A true data blocker is completely passive: no chips, no logic boards, nothing that can negotiate a handshake. OffGrid’s USB-C blockers meet this specification, with physically isolated data pins and EMI-resistant construction.
OffGrid’s USA-made versions extend that assurance through a verified, closed supply chain. For organisations operating under NZ’s Information Security Manual (NZISM) or PSR frameworks, that traceability supports compliance requirements for hardware assurance and procurement transparency.
As the authorised New Zealand distributor for OffGrid, Custodi guarantees genuine, verified-origin hardware – ensuring that every device delivered locally meets the same trusted standards used by forensic and defence agencies worldwide.
A Shared Need – One Principle
Whether it’s a traveler at Auckland Airport, a consultant in Wellington, or an investigator in the field, the environment changes – but the vulnerability doesn’t. Power and data share the same path; risk travels with them.
Across all sectors, the principle is the same: trust no port.
Data blockers aren’t about paranoia – they’re about precision control. They close the smallest but most exploited physical gap in digital security – the USB handshake that shouldn’t happen.
Looking Ahead – The Physical Frontier of Cybersecurity
As USB-C fast charging becomes the standard, the handshake between power and data grows more complex. Even “power-only” cables can exchange metadata as they negotiate voltage and current.
The NCSC NZ emphasises that physical controls remain a cornerstone of effective cyber defence. While encryption protects data in transit, and authentication protects systems, physical safeguards protect the devices themselves.
Future devices may integrate blocking at the circuit level, but today, dedicated external blockers remain the only reliable, universal solution. Custodi sees them as part of a broader digital-hygiene framework – small, tangible tools that uphold New Zealand’s culture of trust, integrity, and privacy.


Trusted Hardware, Trusted Source
Cybersecurity begins with awareness, but it’s enforced through design. In New Zealand, both NCSC NZ and CERT NZ now recommend avoiding public USB charging and using data blockers where needed – the same advice echoed internationally by allied agencies.
For Custodi, that message is clear: physical security is no longer optional. Our mission is to make verified, trusted digital-forensics hardware available across all levels of society – from everyday consumers to government, law enforcement, and defence.
Whether it’s protecting evidence, preserving privacy, or simply ensuring your phone charges safely, the principle is the same: control the connection, protect the data.